Check Point® Software Technologies Ltd.(link is external) announced that U.S. News & World Report has named the company among its 2025-2026 list of Best Companies to Work For(link is external).
Software development teams are driven by speed. Yes, they care about quality and features, but the real pressure is to move fast — faster than the competition.
Security teams are driven by exactly what their title says — security.
Both of which are good and necessary things to deliver what the market wants: Quality products that are the latest and greatest and aren't littered with vulnerabilities that can put users at risk.
But those very different, and often competing, pressures make it difficult for those teams to find common ground. Developers frequently view the security team as an obstacle — the people who slow them down. Security teams tend to view developers as in too much of a rush to care if what they deliver to the market can be easily hacked.
Add to that the reality that many security teams don't understand modern application development practices, including the move to microservices-driven architectures and the use of containers, and the divide gets even wider.
To look more deeply into the specifics of this divide, Synopsys commissioned IT analyst and research firm Enterprise Strategy Group (ESG) to document the dynamics between development and security teams regarding deployment and management of AppSec solutions.
That report, Modern Application Development Security, polled 378 qualified respondents in cybersecurity and application development. They represented several industries including manufacturing, financial services, construction/engineering, and business services, throughout the US and Canada.

And among its key findings was that when there is a contest between speed and security, speed wins. Nearly half (48%) of respondents reported that their organizations knowingly deploy vulnerable code to production due to time pressures.
That finding deserves some context — it doesn't mean organizations and their development teams don't care about security.
First, there is no way to deploy perfect code. So the reality is that while 48% admit to deploying vulnerable code, everybody is doing it some of the time. And that is not always a bad thing. As a recent Gartner paper on DevSecOps put it, "Perfect security and zero risk are impossible." Which means that trying to make code perfect would mean never deploying anything.
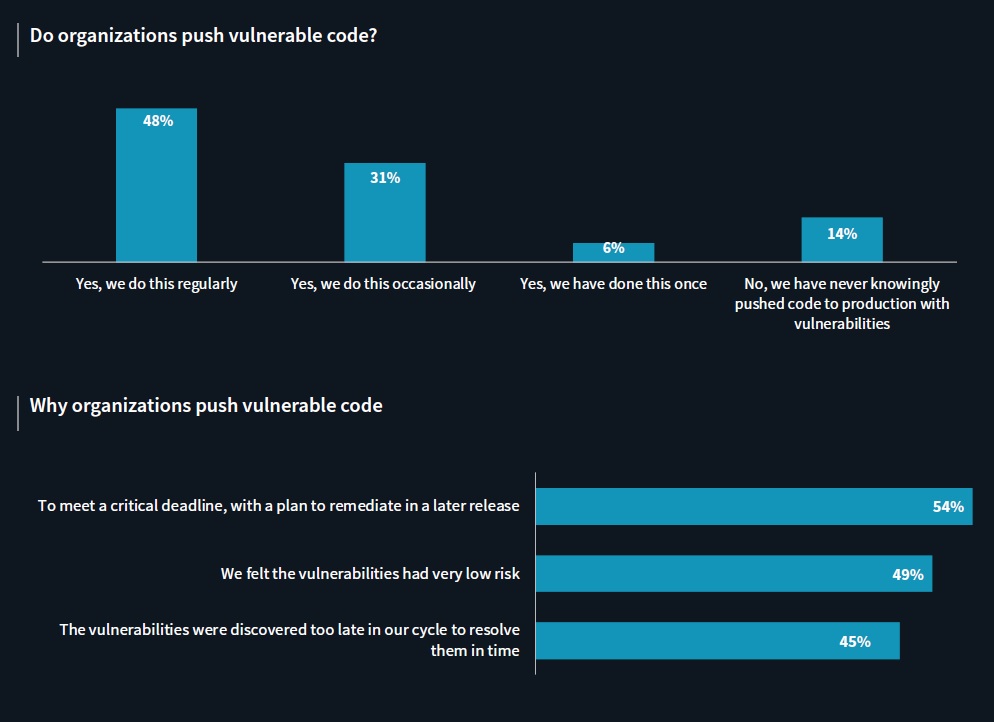
Or, as ESG put it, "Application security requires a constant triage of potential risks … that allow development teams to mitigate risk while still meeting key deadlines for delivery."
However, there is a difference between setting priorities — knowingly letting some lower-risk defects remain — and failing to find more significant vulnerabilities until it is so late in the SDLC that they don't get addressed.
And that is obviously happening. A majority (60%) acknowledged production application exploits involving OWASP Top 10(link is external) vulnerabilities in the past 12 months.

To address that problem takes both people and technology, the report found.
The people part is not a new problem. And what is encouraging is that it is getting lots of attention. Tanya Janca, now founder and security trainer at We Hack Purple Academy but at the time a senior cloud developer advocate for Microsoft, spoke about it more than a year ago at the 2019 RSA conference in San Francisco.
In a presentation titled Security Learns to Sprint: DevSecOps, she said a main reason security isn't more of a core element of the software development life cycle (SDLC) is because development and security teams tend to view one another not just with suspicion, but sometimes outright hostility.
This year, RSA featured an entire day of sessions on how to make DevSecOps teams function more cooperatively and effectively.
But cooperation usually takes understanding. And the less encouraging news is that there is still an understanding gap, in part because of a lack of basic training in security.
Go to New Report: Speed and Security Are Both Possible in Software Development - Part 2
Industry News
Postman announced new capabilities that make it dramatically easier to design, test, deploy, and monitor AI agents and the APIs they rely on.
Opsera announced the expansion of its partnership with Databricks.
Postman announced Agent Mode, an AI-native assistant that delivers real productivity gains across the entire API lifecycle.
Progress Software announced the Q2 2025 release of Progress® Telerik® and Progress® Kendo UI®, the .NET and JavaScript UI libraries for modern application development.
Voltage Park announced the launch of its managed Kubernetes service.
Cobalt announced a set of powerful product enhancements within the Cobalt Offensive Security Platform aimed at helping customers scale security testing with greater clarity, automation, and control.
LambdaTest announced its partnership with Assembla, a cloud-based platform for version control and project management.
Salt Security unveiled Salt Illuminate, a platform that redefines how organizations adopt API security.
Workday announced a new unified, AI developer toolset to bring the power of Workday Illuminate directly into the hands of customer and partner developers, enabling them to easily customize and connect AI apps and agents on the Workday platform.
Pegasystems introduced Pega Agentic Process Fabric™, a service that orchestrates all AI agents and systems across an open agentic network for more reliable and accurate automation.
Fivetran announced that its Connector SDK now supports custom connectors for any data source.
Copado announced that Copado Robotic Testing is available in AWS Marketplace, a digital catalog with thousands of software listings from independent software vendors that make it easy to find, test, buy, and deploy software that runs on Amazon Web Services (AWS).
Check Point® Software Technologies Ltd.(link is external) announced major advancements to its family of Quantum Force Security Gateways(link is external).
Sauce Labs announced the general availability of iOS 18 testing on its Virtual Device Cloud (VDC).












