Check Point® Software Technologies Ltd.(link is external) announced that U.S. News & World Report has named the company among its 2025-2026 list of Best Companies to Work For(link is external).
There might be many people across organizations who claim that they’re using a DevOps approach, but often times, the “best practices” they’re using don’t align with DevOps methodologies. They can say what they do is “DevOps”, but what we’ve found is that many are actually not following basic agile methodology principles, and that’s not DevOps. Ever.
How Are We So Sure?
Electric Cloud gathered data from thousands of engineers and IT leaders across three major events – DOES 2016, Agile 2016 and Appshere 2016 (and compared it with specific data sets from the Puppet and DORA 2016 State of the DevOps Report) – asking them about their deployment and application release automation practices, and we found some interesting patterns.
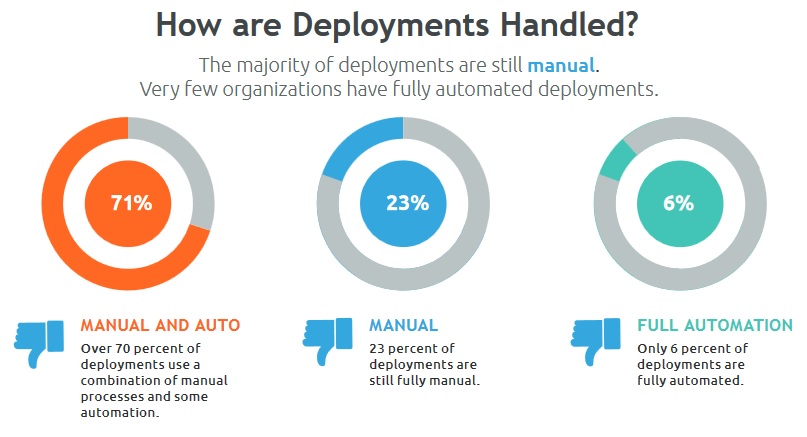
For starters, the data show us that the majority of deployments are still manual. Specifically, over 70 percent of deployments use a combination of manual processes and some automation. While many think, in this instance, that they are automating their releases, this isn’t automation. Just because you’re using a Chef recipe to automate one of your releases, doesn’t mean you’re an automated shop.
It Gets Worse
The two remaining datasets from this section tells us perhaps the most disappointing fact – 23 percent of deployments are still fully manual and only 6 percent of deployments are fully automated. Let’s face it; manual intervention often leads to errors and non-repeatable processes. No bueno. If testing or deployments are handled manually, it’s nearly impossible to implement continuous delivery or continuous integration in any way. What this statistic tells us is that many don’t realize that they have increased the risk of defects to their software (which almost always creates unplanned workloads), or a higher risk of deployments failing all together.
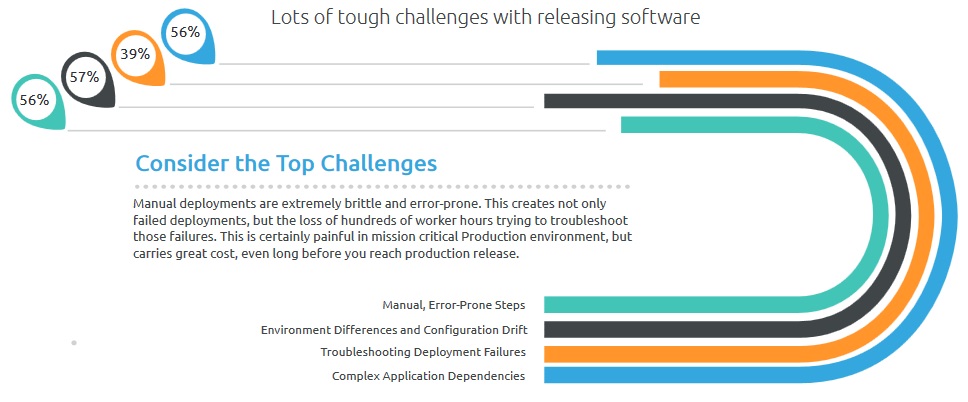
When relying on manual processes versus automation, an entire host of problems can emerge. The top challenges with manual deployments are:
1. Environment differences and configuration drift
2. Manual, error-prone steps
3. Complex application dependencies
4. Manual deployments often lead to more time spent troubleshooting deployment failures
The bottom line is this: manual deployments are extremely brittle and error-prone. This creates not only failed deployments, but also the loss of hundreds of worker hours trying to troubleshoot those failures. This is certainly painful in mission critical production environments, but carries great cost, even long before you reach production release.
The Bigger Truth
As surprising as it might be to read in 2017, IT departments are still struggling to release software at the rate the business demands. As we see from the Puppet and DORA 2016 State of the DevOps Report, automation eliminates common challenges that come with manual deployments, and delivers better results.
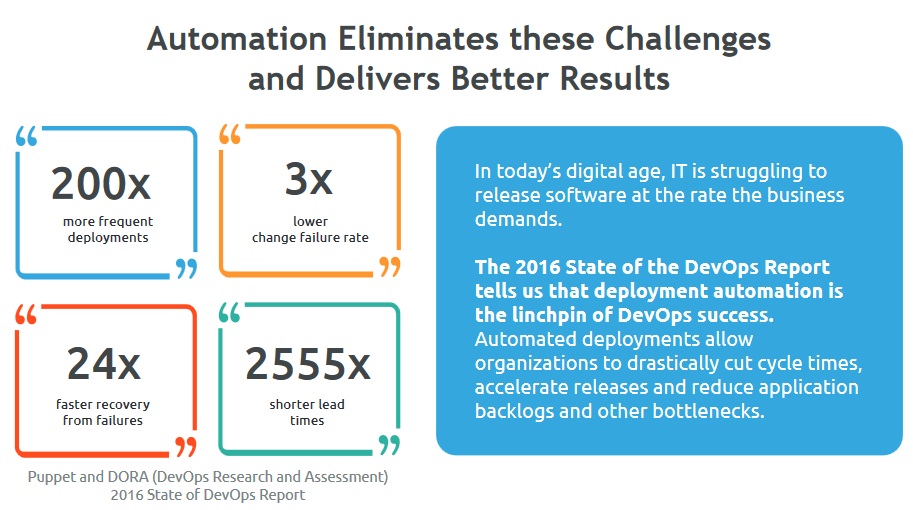
Deployment automation is the linchpin of DevOps success. Automated deployments allow organizations to drastically cut cycle times, accelerate releases and reduce application backlogs. Specifically, according to the Puppet and DORA Report, automation provides 200x more frequent deployments, 3x lower change failure rates, 24x faster recovery from failures and 2555x shorter lead times.
Deployment Automation is the Linchpin of DevOps Success
DevOps is not the responsibility of one person or one team. It’s a company mindset that when set in motion, delivers immediate value. The right Application Release Automation solution can dramatically accelerate your time-to-market and cycle times, give you confidence in your IT operations, enhance teamwork, and reduce operational costs.
Industry News
Postman announced new capabilities that make it dramatically easier to design, test, deploy, and monitor AI agents and the APIs they rely on.
Opsera announced the expansion of its partnership with Databricks.
Postman announced Agent Mode, an AI-native assistant that delivers real productivity gains across the entire API lifecycle.
Progress Software announced the Q2 2025 release of Progress® Telerik® and Progress® Kendo UI®, the .NET and JavaScript UI libraries for modern application development.
Voltage Park announced the launch of its managed Kubernetes service.
Cobalt announced a set of powerful product enhancements within the Cobalt Offensive Security Platform aimed at helping customers scale security testing with greater clarity, automation, and control.
LambdaTest announced its partnership with Assembla, a cloud-based platform for version control and project management.
Salt Security unveiled Salt Illuminate, a platform that redefines how organizations adopt API security.
Workday announced a new unified, AI developer toolset to bring the power of Workday Illuminate directly into the hands of customer and partner developers, enabling them to easily customize and connect AI apps and agents on the Workday platform.
Pegasystems introduced Pega Agentic Process Fabric™, a service that orchestrates all AI agents and systems across an open agentic network for more reliable and accurate automation.
Fivetran announced that its Connector SDK now supports custom connectors for any data source.
Copado announced that Copado Robotic Testing is available in AWS Marketplace, a digital catalog with thousands of software listings from independent software vendors that make it easy to find, test, buy, and deploy software that runs on Amazon Web Services (AWS).
Check Point® Software Technologies Ltd.(link is external) announced major advancements to its family of Quantum Force Security Gateways(link is external).
Sauce Labs announced the general availability of iOS 18 testing on its Virtual Device Cloud (VDC).












