Backslash Security introduced its Fix Simulation and AI-powered Attack Path Remediation capabilities.
As organizations of all sizes are embracing hybrid and multi-cloud infrastructures, they are experiencing the many benefits of a more agile, distributed and high-speed environment where new applications and services can be built and delivered in days and weeks, rather than months and years. But as the adoption of these next generation architectures continues to grow, so do the complexities of securing the cloud workloads running on them.
The results of a recent survey of 350 IT professionals conducted by Alcide and IT Pro indicate that, in 2018, the volume of workloads running in the cloud is growing rapidly, but the workflows and tools to secure these cloud workloads are still highly fragmented and dependent on manual configuration. At a time when security and privacy requirements are more stringent than ever, manually configured workflows are a constraint on business velocity. It is clear there is still an unmet need for end-to-end security solutions that can support frictionless DevOps processes and security professionals in securing cloud workloads in a way that accelerates business outcomes and enhances the organization’s competitive edge.
Hybrid, Multi-Cloud Environments with Distributed Workloads are the New Norm
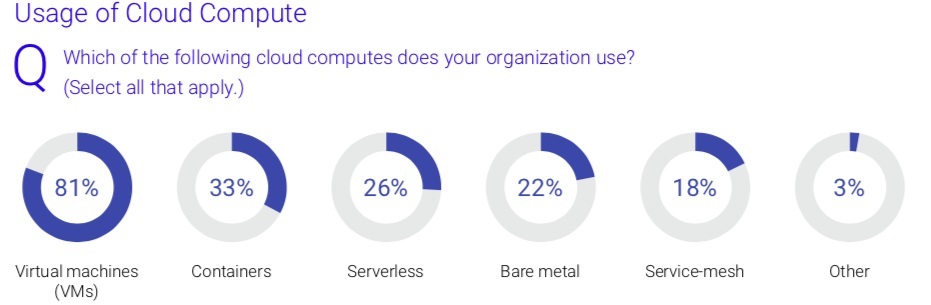
While cloud computing has been around for many years now, the diversification of cloud infrastructure — to hybrid and multi-cloud environments — is becoming more and more common. The survey results confirm that hybrid cloud is now the de facto standard for modern infrastructure; a mix of on-premise and cloud environments. Within those environments, workloads are also distributed across cloud computes: virtual machines (VMs) are the most common environment (83%), with containers (33%), serverless (28%), and service mesh (21%) gaining traction. Though not technically considered types of compute, we still put serverless and service-mesh under the same roof as containers and VMs when we talk about usage.
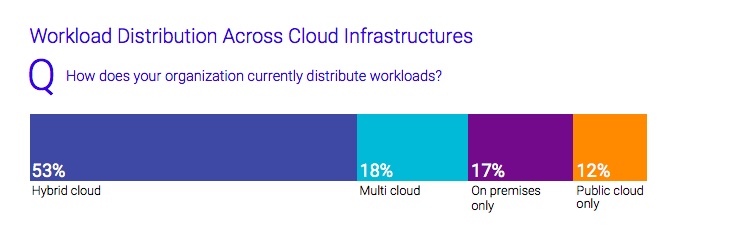
Serverless computing in particular is growing in popularity with 28% of respondents deploying serverless compute within their organizations.
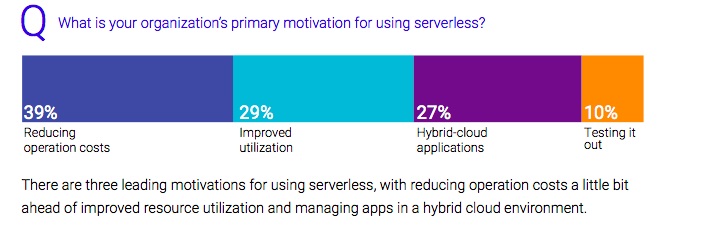
The growing popularity of serverless is attributed to three top motivators including reducing operational costs, improving resource utilization and making the management of apps in a hybrid environment easier.
Despite the many benefits of agile, distributed environments, traditional perimeter-based approaches cannot meet the security requirements of these next-generation apps, and are creating new paradigms based on a shift-left approach that brings security to the app layer early on.
Serverless Security Remains a Question
While the use of containers and serverless continues to expand with the increasingly popular new approaches to software development such as microservices, these new forms of compute require security approaches that span the diverse cloud infrastructure, workloads, and services.
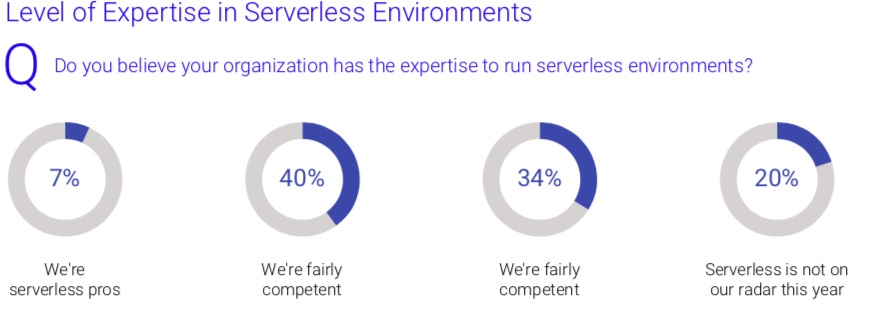
Although added infrastructure complexity is requiring new security methods, there is not yet a widely adopted technique to address these types of environments. Specifically, the report revealed tech. teams are not yet fully confident in the security of their serverless instances. According to the survey, 44% of IT specialists consider their enterprise’s serverless computes to be only "somewhat secure." Additionally, with only 7% believing that their enterprise has a high level of serverless expertise, there is still a learning curve for IT and security teams to know how and when to apply effective security controls in serverless apps.
Overall Complexity of Cloud Security Continues to Grow with Even More Point Solutions
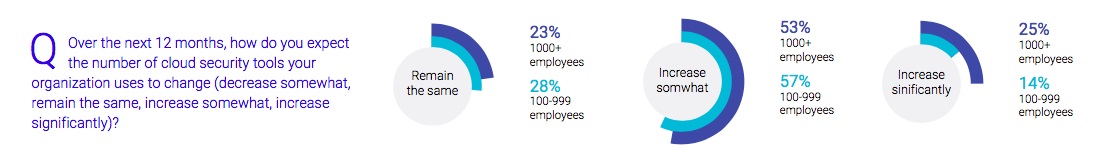
The survey results show that serverless security is not the only area that could be improved in 2019. More broadly, cloud workload security remains extremely fragmented with the number of cloud security tools continuing to expand. Across all company sizes and job types, 75% of the respondents expect their cloud security stack to increase during the next 12 months — either "significantly" (20%) or "somewhat".
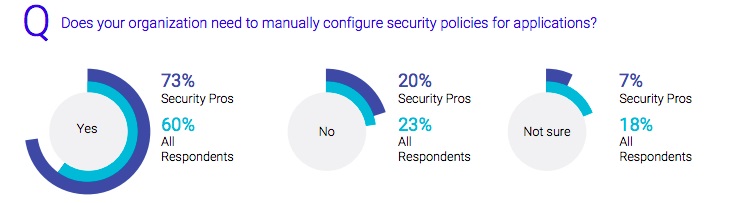
Additionally, cloud workload security configuration has yet to benefit from automation, with nearly three-quarters of security pros reporting that they are still configuring application security policies manually.
Most configurations are highly decentralized: 44% of medium-large enterprises and 74% of very large enterprises have 3 or more people involved in the configuration of security policies for any given app. These time-consuming and error-prone processes often increase vulnerability and business velocity.
Conclusion
Our survey results clearly indicate that cloud security has not yet benefited from the great strides that have been made in automating the security and management of resources and the continuous secured deployment of apps. Innovative, cloud-native, cross-environment security solutions are required to provide effective management and real-time responses to a wide range of attack scenarios. Organizations need unified security controls that span the entire cloud infrastructure, workloads, and services. Additionally, cloud workload security has some catching up to do as manual procedures will no longer cut it in these increasingly distributed environments - automation is critical to consistently implementing corporate security and compliance policies within a holistic and agile framework.
Industry News
Check Point® Software Technologies Ltd. announced the appointment of Nadav Zafrir as Check Point Chief Executive Officer.
Sonatype announced that Sonatype SBOM Manager, its Enterprise-Class Software Bill of Materials (SBOM) solution, and its artifact repository manager, Nexus Repository, are now available in AWS Marketplace, a digital catalog with thousands of software listings from independent software vendors that make it easy to find, test, buy, and deploy software that runs on Amazon Web Services (AWS).
Broadcom unveiled the latest updates to VMware Cloud Foundation (VCF), the company’s flagship private cloud platform.
CAST launched CAST SBOM Manager, a new freemium product designed for product owners, release managers, and compliance specialists.
Zesty announced the launch of its Insights and Automation Platform.
Progress announced the availability of Progress® MarkLogic® FastTrack™, a UI toolkit for building data- and search-driven applications to visually explore complex connected data stored in Progress® MarkLogic® platform.
Snowflake will host the Llama 3.1 collection of multilingual open source large language models (LLMs) in Snowflake Cortex AI for enterprises to easily harness and build powerful AI applications at scale.
Secure Code Warrior announced the availability of SCW Trust Agent – a solution that assesses the specific security competencies of developers for every code commit.
GFT launched AI Impact, a new solution that leverages artificial intelligence to eliminate technical debt, increase developer efficiency and automate critical software development processes.
Code Metal announced a $13M seed, led by Shield Capital.
Atlassian Corporation has achieved Federal Risk and Authorization Management Program (FedRAMP) “In Process” status and is now listed on the FedRAMP marketplace.
Check Point® Software Technologies Ltd. announced that it has received a Leader ranking in The Forrester Wave™: Mobile Threat Defense Solutions, Q3 2024 report.
Mission Cloud announced the launch of Mission Cloud Engagements - DevOps, a platform designed to transform how businesses manage and execute their AWS DevOps projects.
Accelario announces the release of its free TDM solution, including database virtualization and data anonymization.




