SmartBear announced a new version of its API design and documentation tool, SwaggerHub, integrating Stoplight’s API open source tools.
It wasn't long ago when operations, development and security teams didn't talk to each other – and probably sat at different lunch tables in the cafeteria.
Fortunately, when it comes to operations and development, DevOps has changed the traditional compartmentalized style of development by eliminating silos. These teams recognize that operational considerations need to be factored into development decisions from the very beginning, and vice versa to achieve optimal performance.
But what about the security team? Security is largely still siloed from operations and development. No doubt, many DevOps teams have some security controls baked into their automation processes, but a recent survey shows there are still alarming gaps.
Survey Says: The Secret is Out
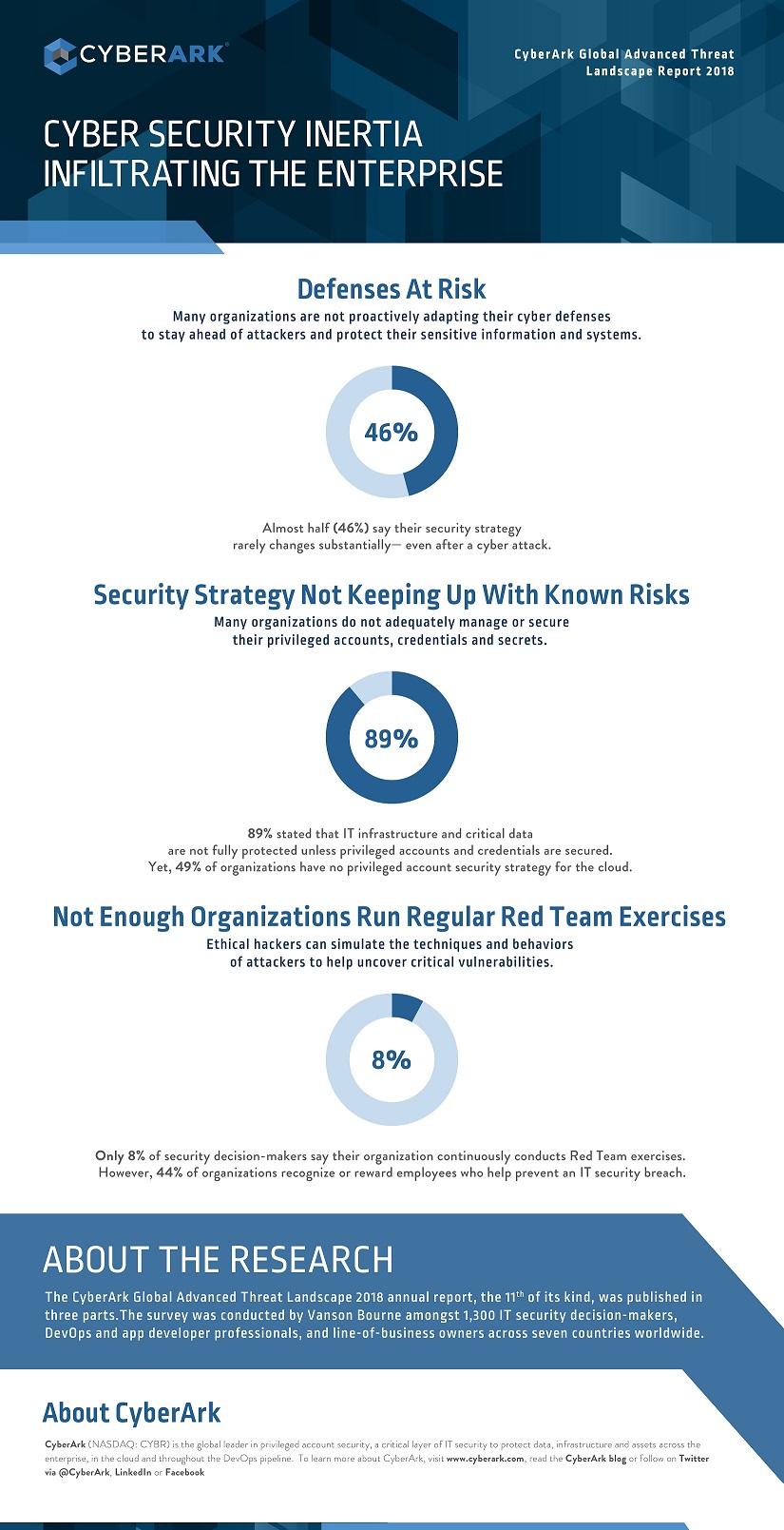
According to the 2018 CyberArk Global Advanced Threat Landscape report, fewer than half of DevOps survey respondents said DevOps and security teams are well integrated and 41 percent say security teams are only brought in at the end of the development cycle. It's hard to defend the notion that security is built into the DevOps process when most organizations admit that DevOps and security teams are not well integrated.
And while development and operations teams can be expected to be knowledgeable about security to a certain point, it is unreasonable to expect them to have the level of security expertise that security teams have acquired through years of experience. The lack of maturity when it comes to DevOps security is made apparent throughout the report.
Many DevOps teams run automatic vulnerability scans or take other measures to eliminate the low hanging security fruit. This is a great first step, but 75 percent of organizations reported they have no privileged account security strategy for DevOps. Even worse, 99 percent of respondents failed to identify the different places privileged accounts or secrets could exist in a DevOps environment.
Privileged accounts, secrets and credentials equal access to an organization's data and infrastructure. With this access, an attacker can impersonate anyone within the organization and take almost anything they want.
Infrastructure-as-code is the engine that fuels DevOps velocity. However, it also means that everything a DevOps team has done, institutional know-how and intellectual property can be more easily stolen.
Making the Case for DevOps Security
Attackers will exploit organizations where they are weak, making unsecured and unmanaged "secrets" – including privileged account credentials, SSH Keys, API keys and more – a new favorite target for attackers.
These secrets are often hardcoded in clear text or publicly accessible, making DevOps a massive security risk to organizations. Attackers know this and are currently exploiting these vulnerabilities and scanning for exposed SSH keys across the internet.
Bottom line – DevOps has changed the game in terms of productivity, but security needs to be a part of the journey. The move from waterfall to agile development has taught us the most efficient time to make a change is at the beginning of the process, which is true of security too.
Security teams need to be included in the DevOps process from the beginning to reduce the cost of changes made later on. Security tools have evolved over time to meet DevOps security teams and not to disrupt DevOps flow or velocity. Any credible security solution will need the ability to be automated and have a small, if not invisible, footprint on DevOps teams.
Industry News
Red Hat announced updates to Red Hat Trusted Software Supply Chain.
Tricentis announced the latest update to the company’s AI offerings with the launch of Tricentis Copilot, a suite of solutions leveraging generative AI to enhance productivity throughout the entire testing lifecycle.
CIQ launched fully supported, upstream stable kernels for Rocky Linux via the CIQ Enterprise Linux Platform, providing enhanced performance, hardware compatibility and security.
Redgate launched an enterprise version of its database monitoring tool, providing a range of new features to address the challenges of scale and complexity faced by larger organizations.
Snyk announced the expansion of its current partnership with Google Cloud to advance secure code generated by Google Cloud’s generative-AI-powered collaborator service, Gemini Code Assist.
Kong announced the commercial availability of Kong Konnect Dedicated Cloud Gateways on Amazon Web Services (AWS).
Pegasystems announced the general availability of Pega Infinity ’24.1™.
Sylabs announces the launch of a new certification focusing on the Singularity container platform.
OpenText™ announced Cloud Editions (CE) 24.2, including OpenText DevOps Cloud and OpenText™ DevOps Aviator.
Postman announced its acquisition of Orbit, the community growth platform for developer companies.
Check Point® Software Technologies Ltd. announced new email security features that enhance its Check Point Harmony Email & Collaboration portfolio: Patented unified quarantine, DMARC monitoring, archiving, and Smart Banners.
Automation Anywhere announced an expanded partnership with Google Cloud to leverage the combined power of generative AI and its own specialized, generative AI automation models to give companies a powerful solution to optimize and transform their business.
Jetic announced the release of Jetlets, a low-code and no-code block template, that allows users to easily build any technically advanced integration use case, typically not covered by alternative integration platforms.
Progress announced new powerful capabilities and enhancements in the latest release of Progress® Sitefinity®.




