GitLab announced the general availability of GitLab Duo Chat.
I will illustrate the parlous state of cybersecurity today (mid-2017) with an analogy. Look at the graph below showing the losing margin of your favorite sports team over a few years:
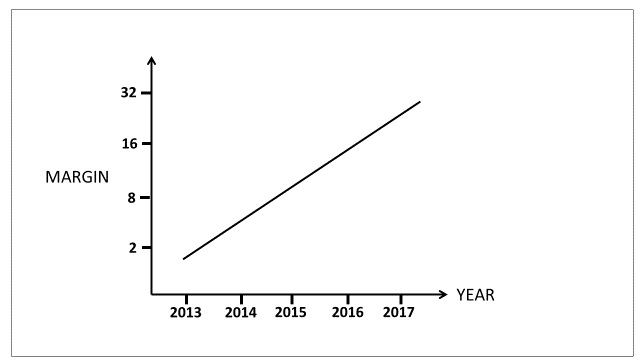
Figure 1: Team Average Losing Margins
What do you recommend the team manager does; resign, buy new team footwear, patch the existing footwear, change their shirt colors? Have their hair cut? No, you might suggest that the team and/or manager is changed radically, taking into account the weaknesses that caused these disastrous losses and mitigating them.
An exact parallel exists today in the field of internet cybersecurity. There is a “team” battling to keep it secure and the opposition who are scoring at will, despite the team's efforts. The number of malware breaches (to use a generic term) are rising in near exponential numbers and, unless there are radical changes, this is set to continue unabated. Most pundits agree with this forecast.
You can find all sorts of numbers by a suitable internet search but the two things they have in common is they are large and increasing.
1. The internet by its very nature is open and, as such, prone to abuse, just like a building without doors or windows.
2. The software which drives the internet was written with openness in mind and not security in mind. It is thus very difficult to retrofit security (or anything else absent from the original design) into it.
3. The result of this is endless patching and re-patching, rather like fixing rust patches on a rust-bucket car only to find another pops up somewhere else on the bodywork.
4. There are factions making money out of selling security hardware, software and services to users and have a vested interest in maintaining the status quo.
5. Current thought puts a lot of the onus on the user (in the most general sense), which I believe is wrong. When I buy an airplane ticket, I don't expect to provide my own life vest, seatbelt and emergency oxygen; that's what I paid my money for. I'll play my part as requested by the cabin staff but that's all.
6. Not only are malware incidents increasing in volume but in sophistication and collateral damage inflicted.
7. The rise of mobile internet access and IoT (Internet of Things) means there is an added dimension to the problem, not to mention two orders of magnitude of potential targets. Targets even today include power stations and simulated attacks on car control systems and this, if nothing else, demands action other than continuous patching, exhortations to the user and hoping for the best.
8. The defense system today cannot cope and hasn't a hope of coping with this new internet security dimension.
9. Any radical new architecture (and an architecture is needed) will involve hardware and software vendors whose products drive the internet in changing their products to conform to this architecture. This conformance will have to be enforced by governments and other large consumers insisting on this conformity by all relevant suppliers. Similar mandates are in force now in some areas.
10. There will be some resistance to a new architecture from anyone who makes money out of the current status of cybersecurity for at least three reasons:
■ The architecture may reduce the need for their products and/or services
■ The wait for an architecture by cautious users will have a similar effect
■ Some of these vendors may be unable to retrofit the architecture onto their current products, originally designed without security in mind.
What is Being Done Today?
More of the same I'm afraid; more exhortations to the users (There have been annual warning to the US President every few year since 1992, saying exactly the same thing; "unless we do something (Mr. President) we are heading for serious trouble" or words to that effect), more selling of solutions and a host of new cyber defense projects across the world by governments, IT organizations and , in some cases, IT vendors. They are being developed in complete isolation (cybersecurity silos) and as a result will almost inevitably be incompatible and will hence fail to communicate with each other.
Trump cybersecurity advisors resign, painting bleak picture of US cyber preparedness
These projects will also be fairly public, rather akin to the NIST output, and the bad guys will love that as they will get advance inklings of what is going on. This has been issuing forth since 1970 and their reports can be numbered in hundreds.
A Few of the Initiatives:
US CNAP (US 2016 Initiative)
FACT SHEET: Cybersecurity National Action Plan
Taking bold actions to protect Americans (But nobody else?) in today's digital world.
UK CSS (UK 2016 Initiative)
NATIONAL CYBER SECURITY STRATEGY 2016-2021
The word "architecture" does not appear in the Govt. paper about the NCSS. It does say: "We want to create a cyber ecosystem in which cyber start-ups proliferate, get the investment and support they need to win business around the world, to provide a pipeline of innovation that channels ideas between the private sector, government and academia."
The Rt. Hon Matt Hancock MP, Minister of State for Digital and Culture [UK National Cyber Security Strategy].
Which is the exact opposite of what is needed. This represents silos within a silo.
The following "initiative" diagram shows the situation diagrammatically:
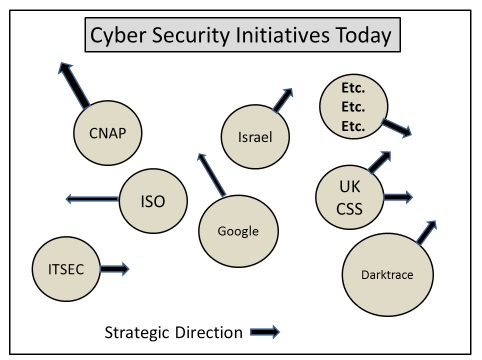
Figure 2: Whither a Cybersecurity Architecture?
Other Cybersecurity Initiatives
There are many, many others to choose from, each adding to the users' confusion as to which to select:
- US Homeland
- Israel
- Google
- FIDO (Fast IDentity Online)
- NATO
- Europol (European Police); cybersecurity is just one aspect
- Darktrace
- Fortinet
- Ingram Micro
- Accenture
- Arbor Networks
- And at least a dozen well-known software vendors working on their own "recipes"
I needn't go on as I feel I have made the point that too many cooks will spoil the (cybersecurity) broth. If the initiatives deliver results, it is highly unlikely that systems using different security architectures of frameworks will communicate without some serious work to provide compatibility.
The outcome is likely to be what we call in England "a dog's breakfast" or, in US terms, "a screw-up."
Industry News
SmartBear announced a new version of its API design and documentation tool, SwaggerHub, integrating Stoplight’s API open source tools.
Red Hat announced updates to Red Hat Trusted Software Supply Chain.
Tricentis announced the latest update to the company’s AI offerings with the launch of Tricentis Copilot, a suite of solutions leveraging generative AI to enhance productivity throughout the entire testing lifecycle.
CIQ launched fully supported, upstream stable kernels for Rocky Linux via the CIQ Enterprise Linux Platform, providing enhanced performance, hardware compatibility and security.
Redgate launched an enterprise version of its database monitoring tool, providing a range of new features to address the challenges of scale and complexity faced by larger organizations.
Snyk announced the expansion of its current partnership with Google Cloud to advance secure code generated by Google Cloud’s generative-AI-powered collaborator service, Gemini Code Assist.
Kong announced the commercial availability of Kong Konnect Dedicated Cloud Gateways on Amazon Web Services (AWS).
Pegasystems announced the general availability of Pega Infinity ’24.1™.
Sylabs announces the launch of a new certification focusing on the Singularity container platform.
OpenText™ announced Cloud Editions (CE) 24.2, including OpenText DevOps Cloud and OpenText™ DevOps Aviator.
Postman announced its acquisition of Orbit, the community growth platform for developer companies.
Check Point® Software Technologies Ltd. announced new email security features that enhance its Check Point Harmony Email & Collaboration portfolio: Patented unified quarantine, DMARC monitoring, archiving, and Smart Banners.
Automation Anywhere announced an expanded partnership with Google Cloud to leverage the combined power of generative AI and its own specialized, generative AI automation models to give companies a powerful solution to optimize and transform their business.
Jetic announced the release of Jetlets, a low-code and no-code block template, that allows users to easily build any technically advanced integration use case, typically not covered by alternative integration platforms.





